Advanced OT & IoT Cybersecurity for Industry 5.0 Core OT Cybersecurity Services

Setting up of “Smart Factory"
Design and deploy secure OT architectures for connected factories.

Microsegmentation
Limit lateral movement by segmenting OT networks and enforcing strict access.
Infrastructure Security
Harden OT devices and networks to reduce attack surface.

OT Penetration Testing
Simulate real attacks to discover and remediate vulnerabilities.

OT Risk Assessment (IEC 62443 + other standards)
Standards-aligned risk assessments and remediation roadmaps.
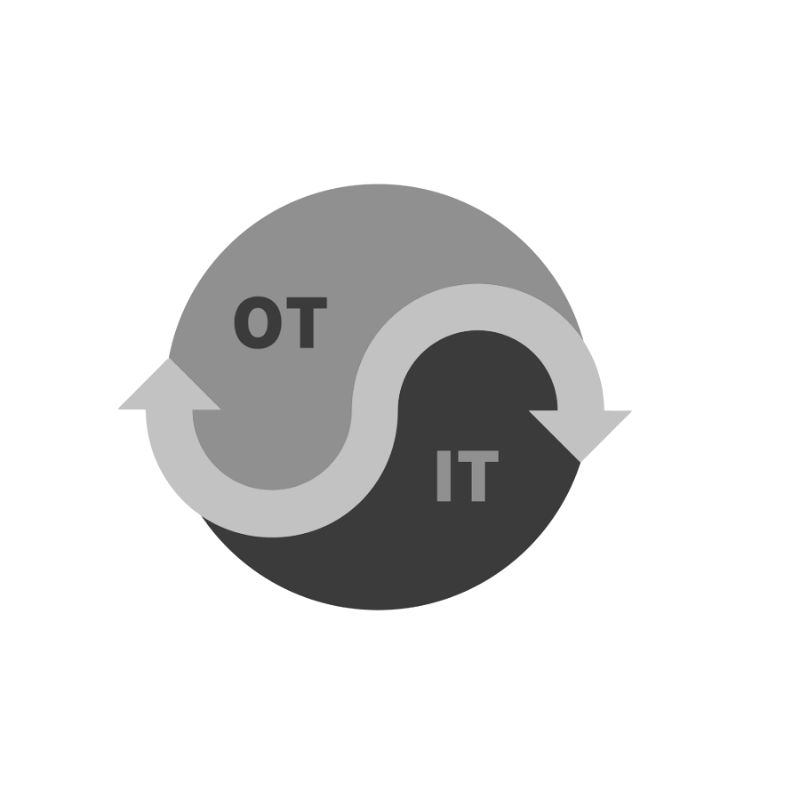
OT–IT Convergence & Security
Secure integration of OT systems with IT and cloud platforms
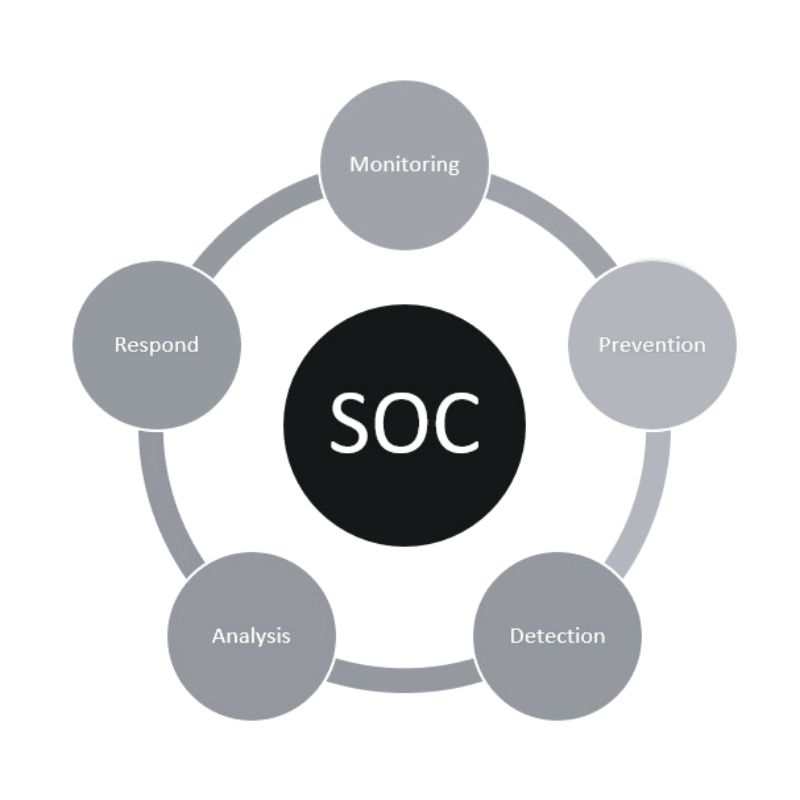
OT SOC Establishment & Continuous Monitoring
Setup OT-aware SOCs with 24/7 monitoring and alerting.

OT Firewall & Network Security Review
Review and strengthen perimeter and internal network defences.

OT Cloud Migration
Securely migrate OT data and workflows to compliant cloud pipelines.
OT Disaster Management & Documentation
Incident response planning, runbooks and disaster recovery documentation.
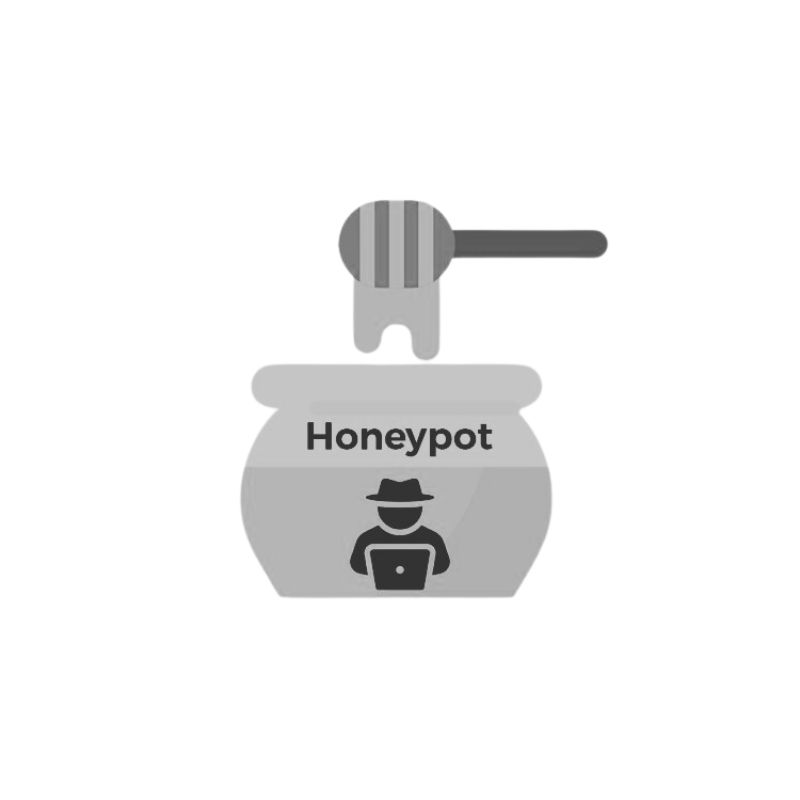
OT Deception Fabric / PlantTrap (OT Honeypot)
Deploy deception environments to detect and analyse intrusions.

OT-Guard — Endpoint & extended detection for operations
Endpoint detection tailored for operational equipment and OT protocols.